Image Stabilization Technology
LEARN MATH FOR WHAT? FOR AVOIDING BLURRY VIDEO! Have you ever recorded a video and found that it was shaking so much that you can’t even finish it? If so, it’s likely that your phone doesn’t have good image stabilization technology! The use of image stabilization in filming devices is very important. Without it, all the videos we watch now would make us feel dizzy. Currently, there are mainly two methods of image stabilization: optical image stabilization (OIS) and electronic image stabilization (EIS). In this article, we will focus on electronic image stabilization technology. OIS technology will be discussed in more detail in the next article.

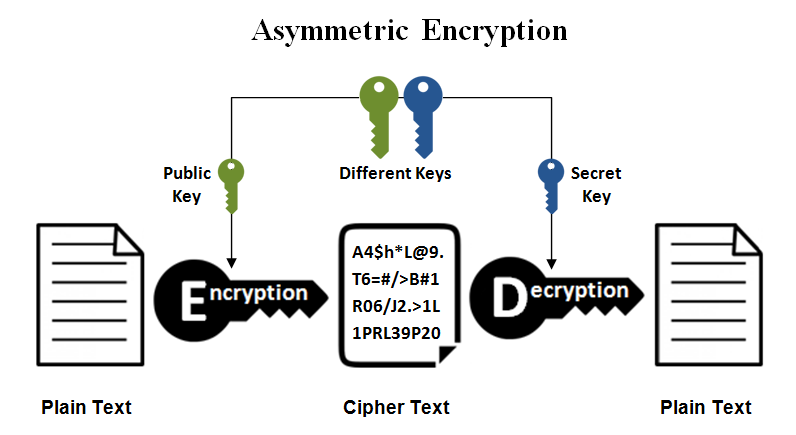 RSA is an asymmetric encryption or public-key cryptography: Data will be encrypted with a public key, but can only be decrypted with the private key of the recipient.
RSA is an asymmetric encryption or public-key cryptography: Data will be encrypted with a public key, but can only be decrypted with the private key of the recipient.